TechInfoDepot:DD-WRT/Ad blocking
Ad blocking @ dd-wrt
Ad Blocking with builds other than Micro
This script, courtesy of several people on the forums, who probably should be named, will enable host-based ad blocking via dns.
Maybe this script will not work on every device or it might crash your router when ther is not enough free ram.
Just put this script into "Startup":
#!/bin/sh
logger WAN up script executing
if test -s /tmp/hosts0
then
rm /tmp/hosts0
fi
logger Downloading http://www.mvps.org/winhelp2002/hosts.txt
wget -O - http://www.mvps.org/winhelp2002/hosts.txt | grep 127.0.0.1 |
sed '2,$s/127.0.0.1/0.0.0.0/g; s/[[:space:]]*#.*$//g;' |
grep -v localhost | tr ' ' '\t' |
tr -s '\t' | tr -d '\015' | sort -u >/tmp/hosts0
grep addn-hosts /tmp/dnsmasq.conf ||
echo "addn-hosts=/tmp/hosts0" >>/tmp/dnsmasq.conf
logger Restarting dnsmasq
killall dnsmasq
dnsmasq --conf-file=/tmp/dnsmasq.conf
...and this into cron:
* 1 * * * root /tmp/.rc_startup
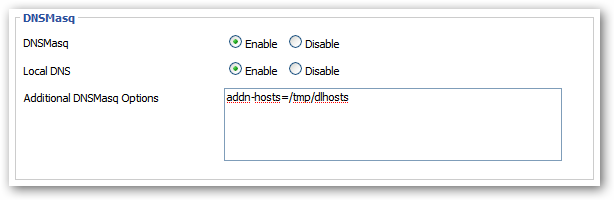
Enable DNSMasq and Local DNS in Services tab; no Additional DNSMasq options necessary.
Ensure cron is enabled.
Ad Blocking with Micro build
The Micro build does not support Journaling Flash File System (JFFS and JFFS v. 2). Because of this, the router can be instructed to block ads (though a hosts file) only on a temporary basis. The hosts file can only be written to temporary memory that is lost with each reboot.
As soon as the router is rebooted, loses electrical power, or is restarted with new settings, you must complete the steps below again, in order to again begin ad blocking.
Unfortunately, the Micro build also does not include most functional commands of the Busybox system, including features that would allow the router to automatically download an updated hosts file itself through a startup script (e.g., the wget command), so you must do it manually. Finally, the Micro build does not include SSH capability, so you must transfer the content of the hosts file by manually pasting it into the router's hosts file through a telnet window, instead of SSH-uploading it to the router.
Steps
1. Download the newest update of a trusted hosts file, such as from MVPS.org at: http://winhelp2002.mvps.org/hosts.txt
2. Open the hosts text file in Notepad, TextEdit, or Notepad++, or another text editor. Highlight all the text in the file and copy it.
3. Go to your router's web interface through your web browser, typically by entering the URL http://192.168.1.1. If you assigned your router a different local IP address, use that instead.
4. In the web interface, click on the Services tab. Enter your DD-WRT router username and password, if prompted.
5. Scroll down to the 'DNSMasq' section. Make sure that DNSMasq bullet and Local DNS bullets are set to 'Enable' that no other DNSMasq options are set.
6. Use Putty or another Telnet client to connect to the router's Telnet interface. (That is, connect to the router's local IP address on port 23 - telnet.)
7. Enter your login and password. The password will be the same as for the web interface. For the username, first try root. If that does not work, try the same username as for the web interface.
8. At the DD-WRT command prompt, type killall DNSMasq and hit enter.
9. Type pwd and hit enter. You should get back "/tmp/root". Type cd .. and hit enter.
10. At the next prompt, type cat > hosts and hit enter.
11. Paste all the text you copied earlier from the hosts.txt file. (For example, in Putty, bring your mouse cursor to the cursor location at the bottom of the telnet window and click your right mouse button to paste.)
12. After a minute or so of the text pasting/transferring, the screen will stop scrolling. When that happens, finish the file with a Ctrl-D key combination.
13. Type dnsmasq --conf-file=/tmp/dnsmasq.conf --addn-hosts=/tmp/hosts and hit enter.
14. You are now finished. Type exit and hit enter.
15. Test out your configuration. Use a computer or connected device to use the local commands "ping" or "tracert" on known good sites (like google.com) vs. sites on the hosts list. The known good sites should have much higher ping times than the sites on the hosts list (for example, 12 ms versus less than 1 ms). The "tracert" (traceroute) comamnd should show a much lengthier Internet path to the good site than the bad site (which should only be one or two hops).
16. Again, repeat all these steps if your router goes down or is rebooted for some reason.
Ad-blocking with DD-WRT revisited (Simple)
Atheros
o0110o @ dd-wrt
startup script:
_rogue=127.0.0.1
echo -e "n=1\nwhile ! wget -q -O /tmp/hsts http://www.mvps.org/winhelp2002/hosts.txt ; do\n\t[ \$n -gt 5 ] && break\n\tlet n+=1\n\tsleep 60\ndone\ngrep \"^127.0.0.1\" /tmp/hsts | grep \"^127.0.0.1\" | grep -v localhost | awk '{print \"$_rogue\\\t\"\$2}' | tr -d '\\\015' >/tmp/dlhosts\nrm /tmp/hsts\nkillall -HUP dnsmasq" >/tmp/wh
sh /tmp/wh &
Additional DNSMasq Options script:
addn-hosts=/tmp/dlhosts
Broadcom
frater @ dd-wrt
I will make 2 seperate threads. One thread is a simple one. It will resolve all those nasty domains to an IP of your choice. In my example I will use 0.0.0.0 but you can also change that to an ip on which you have pixelserv running.
First enable local dns and add the line
addn-hosts=/tmp/dlhosts
And put this in startup code.
_rogue=0.0.0.0
echo -e "#!/bin/sh\nn=1\nwhile sleep 60\ndo\n\twget -q -O - http://www.mvps.org/winhelp2002/hosts.txt | grep \"^127.0.0.1\" | grep -v localhost | awk '{print \"$_rogue\\\t\"\$2}' | tr -d '\\\015' >/tmp/dlhosts\n" >/tmp/write_dlhosts
echo -e "\t[ \`grep -il doubleclick /tmp/dlhosts\` ] && break\n\t[ \$n -gt 5 ] && break\n\tlet n+=1\ndone\nkillall -HUP dnsmasq" >>/tmp/write_dlhosts
chmod +x /tmp/write_dlhosts
/tmp/write_dlhosts &
or this one (which gives the possibility to add some custom hosts in either /opt/etc/hosts or /jffs/hosts):
_rogue=0.0.0.0
echo -e "#!/bin/sh\nn=1\nwhile sleep 60\ndo\n\twget -q -O - http://www.mvps.org/winhelp2002/hosts.txt | grep \"^127.0.0.1\" | grep -v localhost | awk '{print \"$_rogue\\\t\"\$2}' | tr -d '\\\015' >/tmp/dlhosts\n" >/tmp/write_dlhosts
echo -e "\t[ \`grep -il doubleclick /tmp/dlhosts\` ] && break\n\t[ \$n -gt 5 ] && break\n\tlet n+=1\ndone\n[ -e /jffs/hosts ] && cat /jffs/hosts >>/tmp/dlhosts\n[ -e /opt/etc/hosts ] && cat /opt/etc/hosts >>/tmp/dlhosts\nkillall -HUP dnsmasq" >>/tmp/write_dlhosts
chmod +x /tmp/write_dlhosts
/tmp/write_dlhosts &
I will later make another thread where I'll be using the onboard webserver to answer the webcalls.
frater:Posted: Mon Jun 08, 2009 7:02 am
With this script you can exclude some hosts and include others...
This is the script on MY router. I have an USB-stick, so I prefer to have my "dlhosts" on there....
If you have only jffs as permanent storage, you should change
_f=/opt/dlhosts
into
_f=/tmp/dlhosts
In /opt/etc/ I have a file called "hosts" its contents will be blindly added.
In /opt/etc I als have a file called "dlhosts.exclude" in which I have the domains which should be stripped.
If you want to place them in /jffs you should change:
stor=/opt/etc
into
stor=/jffs
_rogue=192.168.10.5
wr=/tmp/write_dlhosts
echo -e "#!/bin/sh\nstor=/opt/etc\nxcl=\$stor/dlhosts.exclude\n_f=/opt/dlhosts\nn=1\nwhile sleep 60\ndo\n\twget -q -O - http://www.mvps.org/winhelp2002/hosts.txt | grep \"^127.0.0.1\" | grep -v localhost | awk '{print \"$_rogue\\\t\"\$2}' | tr -d '\\\015' >\$_f\n" >$wr
echo -e "\t[ \`grep -il doubleclick \$_f\` ] && break\n\t[ \$n -gt 5 ] && break\n\tlet n+=1\ndone\n[ -e \$stor/hosts ] && cat \$stor/hosts >>\$_f" >>$wr
echo -e "if [ -e \$xcl ] ; then\n\twhile read khost ; do\n\t\tsed -i -e \"s/$_rogue\\\t\${khost}/#/\" \$_f\n\tdone < \$xcl\nfi\nkillall -HUP dnsmasq" >>$wr
chmod +x $wr
$wr &
It will create a script called write_dlhosts in /tmp If you want to look at the code in a more readable form you should look at that one first
Happy testing...